If you ever worked with the Kubernetes Dashboard you certainly have noticed the rather short session timeout (about 10 minutes).
By adjusting the startup parameters you can either:
- Increase the timeout
- Disable the timeout
- Skip authentication altogether
Skipping the authentication is useful in a dev environment where you don’t need or want authentication.
Dashboard v2
NOTE: the startup-args also work for the new v2.0.0-beta2 dashboard.
The difference is that the v2 dashboard is deployed in its own namespace kubernetes-dashboard:
$ kubectl -n kubernetes-dashboard describe deployments kubernetes-dashboard
spec:
containers:
- args:
- --auto-generate-certificates
- --namespace=kubernetes-dashboardAlso note the new (undocumented) Dashboard Login URL.
Change parameters on the command line
The v1.x dashboard is usually deployed in the kube-system namespace:
$ kubectl -n kube-system get deployments
NAME READY UP-TO-DATE AVAILABLE AGE
coredns 2/2 2 2 30d
fallacious-serval-metrics-server 1/1 1 1 13d
kubernetes-dashboard 1/1 1 1 29d
tiller-deploy 1/1 1 1 30dAnd has a single startup argument (Args: --auto-generate-certificates):
$ kubectl -n kube-system describe deployments kubernetes-dashboard
Name: kubernetes-dashboard
Namespace: kube-system
CreationTimestamp: Wed, 26 Jun 2019 14:20:03 +0200
Labels: k8s-app=kubernetes-dashboard
Annotations: deployment.kubernetes.io/revision: 2
kubectl.kubernetes.io/last-applied-configuration:
{"apiVersion":"apps/v1","kind":"Deployment","metadata":{"annotations":{},"labels":{"k8s-app":"kubernetes-dashboard"},"name":"kubernetes-da...
Selector: k8s-app=kubernetes-dashboard
Replicas: 1 desired | 1 updated | 1 total | 1 available | 0 unavailable
StrategyType: RollingUpdate
MinReadySeconds: 0
RollingUpdateStrategy: 25% max unavailable, 25% max surge
Pod Template:
Labels: k8s-app=kubernetes-dashboard
Service Account: kubernetes-dashboard
Containers:
kubernetes-dashboard:
Image: k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
Port: 8443/TCP
Host Port: 0/TCP
Args:
--auto-generate-certificates
...Edit the kubernetes-dashboard deployment and add --token-ttl=0 to the containers-args to disable the session timeout.
If you want to disable authentication altogether additionaly add --enable-skip-login:
$ kubectl -n kube-system edit deployments kubernetes-dashboard
...
spec:
containers:
- args:
- --auto-generate-certificates
- --token-ttl=0
...Save and close and wait for the POD to be restarted. You’ll see the additional startup-argument --token-ttl=0 in the pod as well:
$ kubectl -n kube-system describe pod kubernetes-dashboard-XXXX-YYYYChange parameters with the GUI
Select namespace kube-system and go to Deployments.
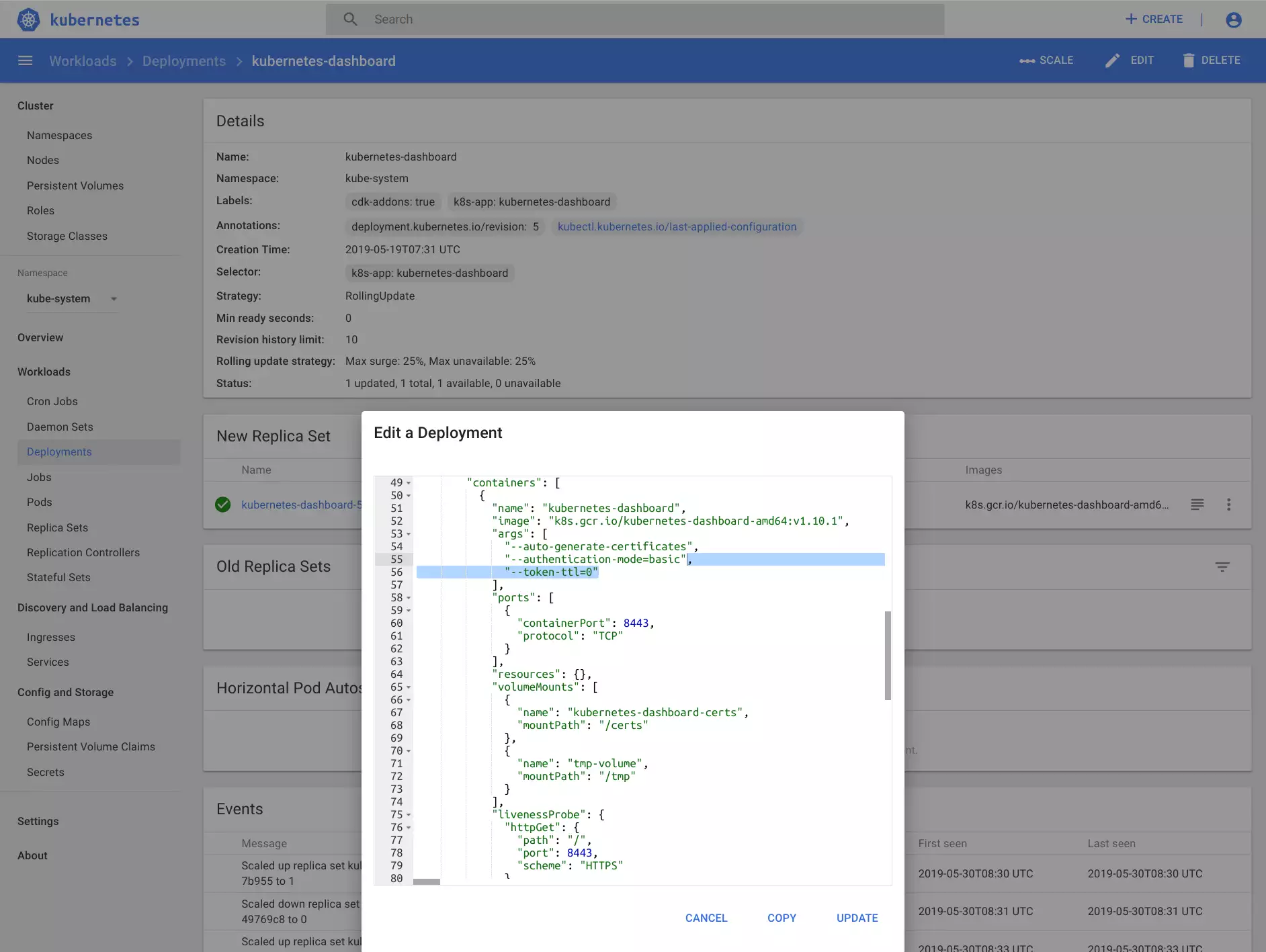
Select the kubernetes-dashboard and add --token-ttl=0 to the containers-args:
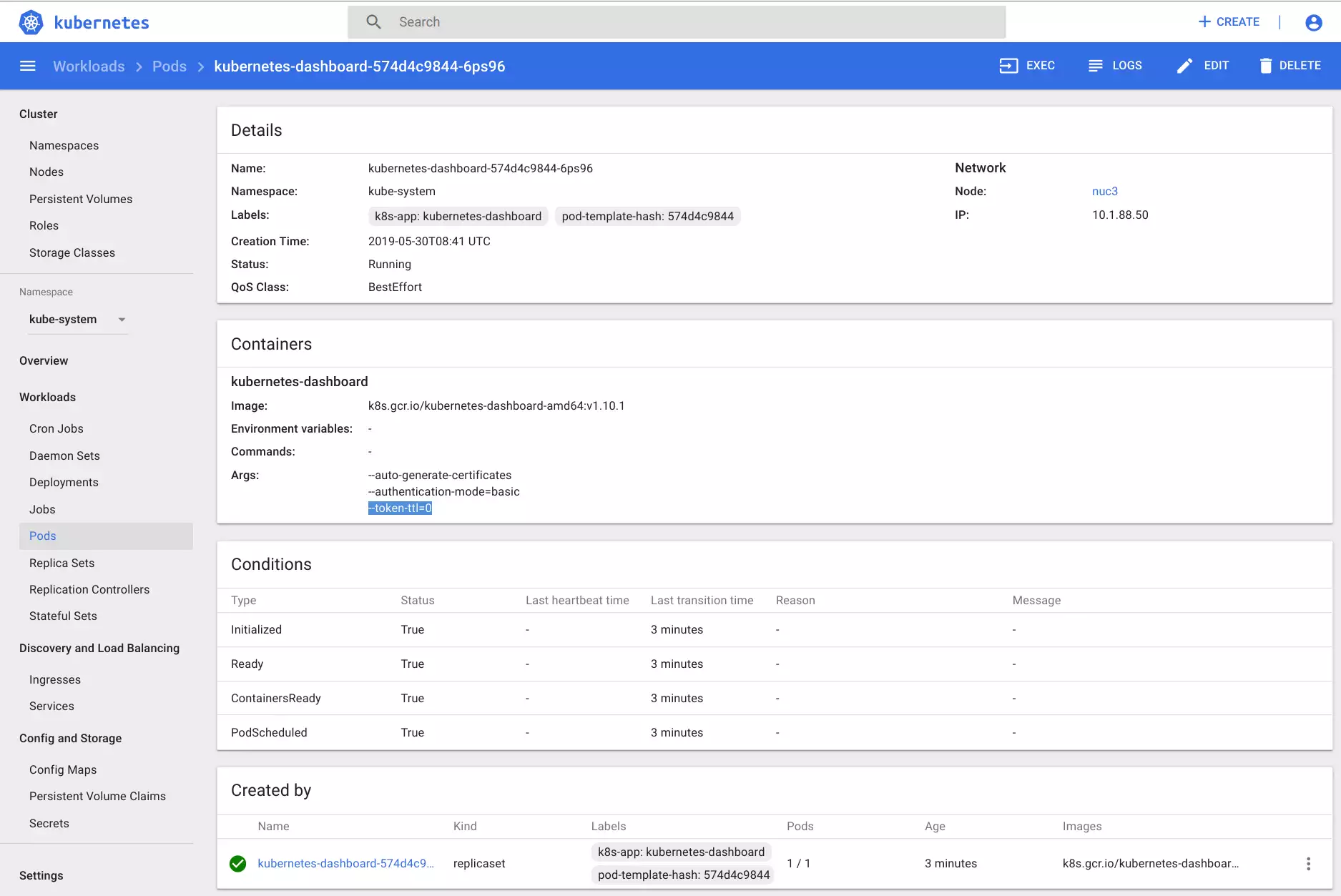
Double check that the corresponding pod (which was created after the beforementioned change) has a new startup argument:
Disable login
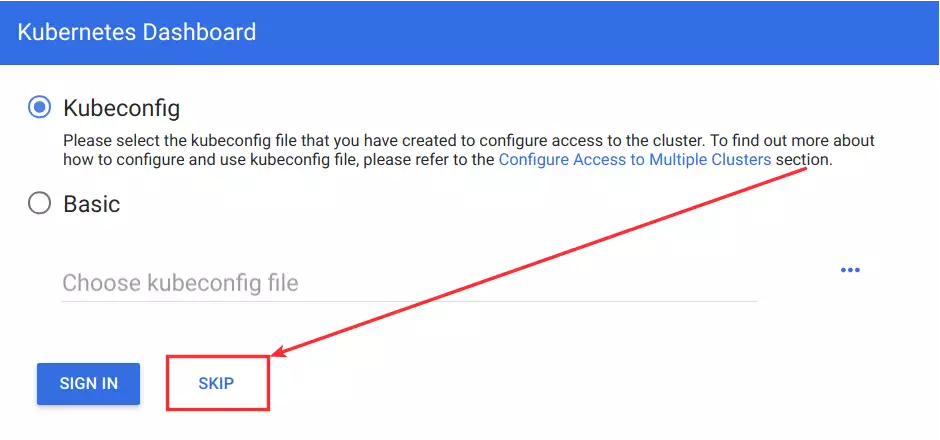
If you’re using a dashboard version >= v1.10.1 there’s an option to disable the login altogether:
--enable-skip-login"args": [
"--auto-generate-certificates",
"--authentication-mode=basic",
"--token-ttl=0",
"--enable-skip-login"
],This will add a Skip button to the dashboard:
Startup parameters for a Juju/Conjure-up dashboard
If you have deployed the dashboard with a conjure-up/juju spell:
$ juju config kubernetes-master enable-dashboard-addons=truethe dashboard deployment (and pods) have an annotation: labels: {cdk-addons: 'true', k8s-app: kubernetes-dashboard}.
You cannot really change the startup arguments of the dashboard because there is a watchdog which resets your changes to the default of the snap.
You can either remove the annoation (which basically breaks the snap automation) - or - disable the out-of-the-box deployment for the dashboard with:
$ juju config kubernetes-master enable-dashboard-addons=falseand deploy your custom dashboard configuration:
$ kubectl apply -f kubernetes-dashboard.yamlDevelopment notes
NOTE: Log in to the master node and check the logs to understand how juju works/deploys the addons:
Command '['/snap/cdk-addons/900/kubectl', 'apply', '-f', '/root/snap/cdk-addons/900/addons', '--recursive', '-l', 'cdk-addons=true', '--force']'Next copy the snap to your own directory:
scp -r /root/snap/cdk-addons/900/addons blinkeye@10.10.10.10:/tmp/kubernetes/Adjust kubernetes-dashboard.yaml:
git diff kubernetes-dashboard.yaml
diff --git a/kubernetes/kubernetes-dashboard.yaml b/kubernetes/kubernetes-dashboard.yaml
index 27378fd..aea54e0 100644
--- a/kubernetes/kubernetes-dashboard.yaml
+++ b/kubernetes/kubernetes-dashboard.yaml
@@ -1,7 +1,7 @@
apiVersion: v1
kind: Secret
metadata:
- labels: {cdk-addons: 'true', k8s-app: kubernetes-dashboard}
+ labels: {k8s-app: kubernetes-dashboard}
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
@@ -9,14 +9,14 @@ type: Opaque
apiVersion: v1
kind: ServiceAccount
metadata:
- labels: {cdk-addons: 'true', k8s-app: kubernetes-dashboard}
+ labels: {k8s-app: kubernetes-dashboard}
name: kubernetes-dashboard
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
- labels: {cdk-addons: 'true'}
+ labels: {}
name: kubernetes-dashboard-minimal
namespace: kube-system
rules:
@@ -46,7 +46,7 @@ rules:
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
- labels: {cdk-addons: 'true'}
+ labels: {}
name: kubernetes-dashboard-minimal
namespace: kube-system
roleRef: {apiGroup: rbac.authorization.k8s.io, kind: Role, name: kubernetes-dashboard-minimal}
@@ -56,7 +56,7 @@ subjects:
apiVersion: apps/v1
kind: Deployment
metadata:
- labels: {cdk-addons: 'true', k8s-app: kubernetes-dashboard}
+ labels: {k8s-app: kubernetes-dashboard}
name: kubernetes-dashboard
namespace: kube-system
spec:
@@ -69,7 +69,7 @@ spec:
labels: {k8s-app: kubernetes-dashboard}
spec:
containers:
- - args: [--auto-generate-certificates, --authentication-mode=basic]
+ - args: [--auto-generate-certificates, --authentication-mode=basic, --token-ttl=0, --enable-skip-login]
image: k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
livenessProbe:
httpGet: {path: /, port: 8443, scheme: HTTPS}
@@ -93,7 +93,7 @@ spec:
apiVersion: v1
kind: Service
metadata:
- labels: {cdk-addons: 'true', k8s-app: kubernetes-dashboard}
+ labels: {k8s-app: kubernetes-dashboard}
name: kubernetes-dashboard
namespace: kube-system
spec:
Metrics server
Disable the metrics server from the juju charm:
$ juju config kubernetes-master enable-metrics=falseUpdate helm and install:
$ helm update
$ helm install --namespace kube-system stable/metrics-server
NAME: dangling-giraffe
LAST DEPLOYED: Tue Jun 11 16:24:33 2019
NAMESPACE: kube-system
STATUS: DEPLOYED
RESOURCES:
==> v1/ClusterRole
NAME AGE
system:dangling-giraffe-metrics-server 0s
system:metrics-server-aggregated-reader 0s
==> v1/ClusterRoleBinding
NAME AGE
dangling-giraffe-metrics-server:system:auth-delegator 0s
system:dangling-giraffe-metrics-server 0s
==> v1/Deployment
NAME READY UP-TO-DATE AVAILABLE AGE
dangling-giraffe-metrics-server 0/1 1 0 0s
==> v1/Pod(related)
NAME READY STATUS RESTARTS AGE
dangling-giraffe-metrics-server-5454697454-t29j8 0/1 ContainerCreating 0 0s
==> v1/Service
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dangling-giraffe-metrics-server ClusterIP 10.152.183.109 <none> 443/TCP 0s
==> v1/ServiceAccount
NAME SECRETS AGE
dangling-giraffe-metrics-server 1 0s
==> v1beta1/APIService
NAME AGE
v1beta1.metrics.k8s.io 0s
==> v1beta1/RoleBinding
NAME AGE
dangling-giraffe-metrics-server-auth-reader 0s
NOTES:
The metric server has been deployed.
In a few minutes you should be able to list metrics using the following
command:
kubectl get --raw "/apis/metrics.k8s.io/v1beta1/nodes"