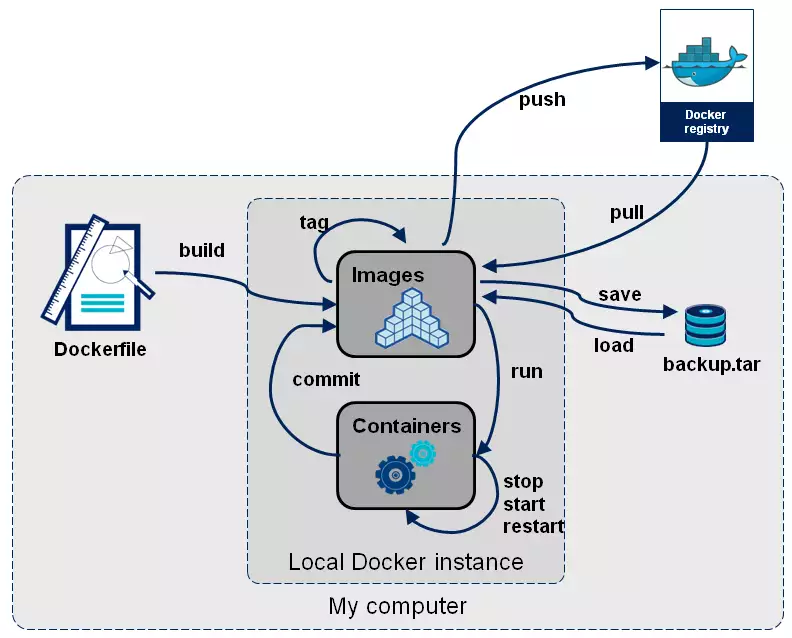
User your own private docker registry for development or private/non-public projects.
Docker Setup
Start registry container:
$ docker run -d -p 5000:5000 --restart=always --name registry registry:2check container:
$ docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
d27ee6ca3baa registry:2 "/entrypoint.sh /etc…" 24 minutes ago Up 2 seconds 0.0.0.0:5000->5000/tcp registryand version:
$ docker exec d27ee6ca3baa registry -v
registry github.com/docker/distribution v2.7.1try to login:
$ docker login http://10.10.10.10:5000
Authenticating with existing credentials...
Login did not succeed, error: Error response from daemon: Get https://10.10.10.10:5000/v2/: http: server gave HTTP response to HTTPS clientAdjust or create a docker config (use proper ip/netmask):
cat <<EOF >/etc/docker/daemon.json
{
"insecure-registries": ["10.10.10.0/24"]
}
EOFrestart docker:
$ sudo service docker restartand log in again:
$ docker login https://10.10.10.10:5000
Authenticating with existing credentials...
Login SucceededKubernetes Setup
Reference: Kubernetes: Pull an Image from a Private Registry
Create a docker configuration file similar to the one you have in ~/.docker/config.json:
cat <<EOF >docker-config.json
{
"auths": {
"10.10.10.10:5000": {
"auth": "YmxpbmtleWUuY2g6ZDBjazNyLmMwbQ=="
},
"https://index.docker.io/v1/": {
"auth": "YmxpbmtleWUuY2g6ZDBjazNyLmMwbQ=="
}
},
"HttpHeaders": {
"User-Agent": "Docker-Client/18.09.5 (linux)"
}
}
EOFNow create a kubernetes secret from this docker-config.json file with:
$ kubectl create secret generic regcred --from-file=.dockerconfigjson=docker-config.json --type=kubernetes.io/dockerconfigjson
secret/regcred created
# verify
$ kubectl get secret regcred --output=yaml
apiVersion: v1
data:
.dockerconfigjson: ...
kind: Secret
metadata:
creationTimestamp: "2019-05-29T14:01:36Z"
name: regcred
namespace: default
resourceVersion: "1779592"
selfLink: /api/v1/namespaces/default/secrets/regcred
uid: 45cca5fe-821a-11e9-a954-525400fe342c
type: kubernetes.io/dockerconfigjsonNOTE: auth is just base64 encoded username:password, e.g.:
$ echo "username:password" | base64
dXNlcm5hbWU6cGFzc3dvcmQKand to decode:
$ echo "dXNlcm5hbWU6cGFzc3dvcmQK" | base64 -d
username:passwordNext, on each Kubernetes Node allow insecure registries:
cat >/etc/docker/daemon.json <<EOF
{
"insecure-registries": ["10.10.10.0/24"]
}
EOFThen restart the docker daemon:
$ service docker restart
$ docker login 10.10.10.10:5000Docker registry cleanup
Log in to the registry container:
$ docker exec -it registry /bin/shthen:
$ cd /var/lib/registry/docker/registry/v2/repositories
$ rm -r old_repositoryDouble check (from outside):
$ curl -X GET localhost:5000/v2/_catalogReason: the docker container with the registry does not have Curl installed.
Docker cleanup
Everything
$ docker system prune --volumes -fRemove
Remove all non-running containters.
$ docker ps -a | grep Exited | awk '{print $1}' | xargs docker rmNext remove unused images:
$ docker image prune -a
WARNING! This will remove all images without at least one container associated to them.
Are you sure you want to continue? [y/N] y
Deleted Images:
untagged: k8s.gcr.io/pause:3.1
untagged: k8s.gcr.io/pause@sha256:f78411e19d84a252e53bff71a4407a5686c46983a2c2eeed83929b888179acea
deleted: sha256:da86e6ba6ca197bf6bc5e9d900febd906b133eaa4750e6bed647b0fbe50ed43e
deleted: sha256:e17133b79956ad6f69ae7f775badd1c11bad2fc64f0529cab863b9d12fbaa5c4
...also see: https://gist.github.com/bastman/5b57ddb3c11942094f8d0a97d461b430